Search This Blog
We provide data, new trends, actors, intelligence, market dynamics (drivers, opportunities, restraints, challenges, etc.), analytics, advisory, technologies (apps, software, systems, algorithm, etc.), services, market data (consumers, revenue, investments, capital, etc.), actionable insights, information, consulting, etc.
Posts
Showing posts from February 11, 2015
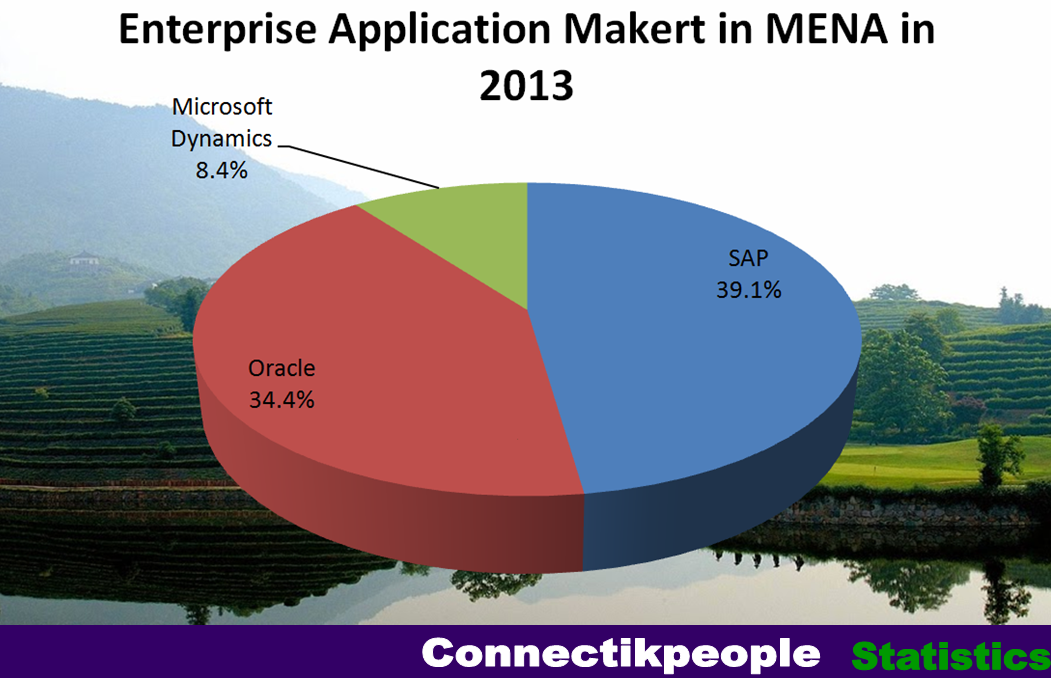
Arab Middle East and North Africa Enterprise Application Software Market 2013–2018.
- Get link
- Other Apps
New Red Hat Certified Architect Concentrations for technology professionals.
- Get link
- Other Apps
Develop and Launch Cybersecurity Startups in our digital-driven world.
- Get link
- Other Apps
Box Enterprise Key Management in our data-driven age.
- Get link
- Other Apps
Microsoft Critical Security Bulletins and Security Update for Chrome OS.
- Get link
- Other Apps
Contextual Marketing Platform in our digital age: stakes, realities and recommendations.
- Get link
- Other Apps