Warning: BackDoor.Saker.1, the malignant program capable of bypassing (UAC) according to Doctor Web.
 For those, who unfamiliar, Connectikpeople may
recall that, Doctor Web is a Russian anti-virus company. In its commitment to
help secure and improve your online presence, the company announced having
detected a malignant program BackDoor.Saker.1, which is capable of bypassing the User Account
Control (UAC).
For those, who unfamiliar, Connectikpeople may
recall that, Doctor Web is a Russian anti-virus company. In its commitment to
help secure and improve your online presence, the company announced having
detected a malignant program BackDoor.Saker.1, which is capable of bypassing the User Account
Control (UAC).
According to Doctor Web the program's main
function is to execute directives from
criminals and, most importantly, to intercept user keystrokes (keylogging).
criminals and, most importantly, to intercept user keystrokes (keylogging).
Based on certain notes reported by Dr Web, Connectikpeople has observed
that the Trojan launches the file temp.exe to bypass the UAC. The file extracts
a library to bypass the UAC and injects its code into the process explorer.exe,
after which the library is saved into a system folder. Then, upon launching the
utility sysrep, the library code launches the malignant application ps.exe. In
turn, this file saves another library to a different folder. The library file
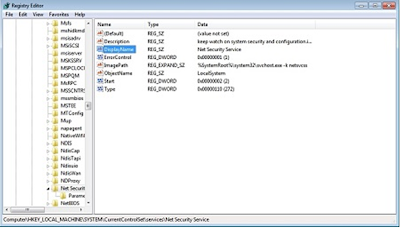
is registered in the Windows Registry as a service with the name "Net Security
Service" and the following description: “keep watch on system security and
configuration.if this service is stopped, protected content might not be down
loaded to the device”. This library contains the main backdoor
payload.
Dr.Web, added: ‘’when launched, BackDoor.Saker.1 collects
information about the compromised system, including the Windows version, CPU
frequency, available RAM, computer name, user login and the hard disk serial
number, and transmits it to criminals. Next, the Trojan creates a file in a
system folder into which user keystrokes are logged. After this, the backdoor
awaits a remote server’s response, which may involve commanding the backdoor to
reboot, shut down, remove itself, start a separate thread to execute commands
via a shell, or even run its own file manager which can upload files from an
infected machine, download files via the network, create folders, and delete,
move and run files’’.
Therefore, if infected Connectikpeople recommends you, users or administrators
to restore your system. Dr.Web announced that the threat's signature has been
added to Dr.Web virus databases.